Notifications
CROWN MARKET : Gained popularity in the Dark Web due to its focus on security and privacy. It provided a secure platform for buyers and sellers, implementing features such as escrow services and encrypted communications. CrownMarket primarily dealt with drugs, Cloned cards, fake counterfeits notes offering high-quality products and reliable service to its users with super fast and discreet delivery.
Currently one of the biggest and most reputable marketplaces since the fall of Hydra Market. Made a name for itself in a very short time interval. On top of a user friendly interface and top vendors, below are some of the features that come with this marketplace:
crownozv6lvy373fkx44o2mxrlst4b6pu6zttcmquueomcw4onmm7oad.onion
crownipsgwzaj3eby5pienlzanam5qjreedgvvqlctlkllx7l2x4nyyd.onion
—–BEGIN PGP PUBLIC KEY BLOCK—–
Version: BCPG v1.58
mI0EZnPx3AEEAM97l3q0X4MwS/bdBMurlZfydxX4/AicJRYiZ7EHnSb1lSE6MLkw
uLuuTDptT9zM+2IpmJGKj+3RMawOlfd5/g0uYvDdZYY9raIrv+qpStt6m2I5+8nn
6aeoi+2LREGG0eMP1gfvx089j8Ci77/WEX2oPElrtz+gh7J+wUBeFhkrABEBAAG0
BmJpZ2RvZ4icBBABAgAGBQJmc/HcAAoJEC0W0ZagHe+1lIUEALsiKdU1CjTQLJXC
U2nKbjfZ0AKMmag5STucGgBp5XSgJc0v6w2hLQ3s3kCZLaHYy4evtwFHuunK7Y0o
55uqh2A8xUlsc5FtyALyb9Sbo9LLuwjqDYo7flXm+uHuAx91p1cgV49R4zC4bC+l
p5qmiR8yoiQhilUBfhnuT2nVotD3
=sq6y
—–END PGP PUBLIC KEY BLOCK—–
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA256
crownozv6lvy373fkx44o2mxrlst4b6pu6zttcmquueomcw4onmm7oad.onion
crownipsgwzaj3eby5pienlzanam5qjreedgvvqlctlkllx7l2x4nyyd.onion
—–BEGIN PGP SIGNATURE—–
Version: OpenPGP.js v4.10.10
Comment: https://openpgpjs.org
wrMEAQEIAAYFAmck9PkAIQkQLRbRlqAd77UWIQTK2/AbBJl1bOq4yfotFtGW
oB3vteCqA/sGN3zJGBKuK1/cnOaNoITMMFK/jMfIqvZS8BKBE8R0bYJaVpm+
A8R9GRIUkfEXZ9GeYzsQ57b3wLBhVGIJuG7Y9/23u2cgJNSfIZtmkyy8AcwH
Q+9s67/E43piBL/+ka9ZpeOH9mUx8JMdrc6j2YhLS96S83YoyPskVytrc85b
jw==
=90FB
—–END PGP SIGNATURE—–
The Tor proxy is a powerful tool that allows users to browse the internet anonymously and securely. If you’re someone who values online privacy, or if you’re looking for a way to access content from a region-restricted network, the Tor proxy could be your solution. Let’s break down what it is, how it works, and why it’s become essential for many internet users today. Visit crown market here
At its core, the Tor proxy refers to a privacy-focused network designed to protect your online identity by masking your IP address. Tor, short for The Onion Router, works by routing your internet traffic through multiple layers of encryption, known as “onions.” These layers ensure that no one can trace your online activities back to your device or identity.
The way the proxy works is incredibly unique and effective at maintaining user anonymity. When you connect to Tor, your internet data is relayed through a series of volunteer-operated servers around the world. Each server only knows about the one before it and the one after it, making it nearly impossible for anyone to track your browsing activity. This technique, known as onion routing, ensures that your browsing is private and secure.
There are many reasons why someone might choose to use a proxy:
For these reasons, Tor has become a trusted choice for users looking to maintain their privacy online, from journalists and activists to everyday internet users.
While both Tor proxies and VPNs are privacy tools, they work quite differently. A VPN encrypts your internet traffic and routes it through a server, changing your IP address in the process. However, a Tor proxy uses multiple nodes in a distributed manner, providing an additional layer of encryption, making it a bit more difficult to trace your activity back to you.
Tor is also free to use, unlike most VPN services that require a subscription.
Tor’s security features are solid, but like any tool, there are potential risks. While it does an excellent job of hiding your IP and encrypting data, Tor users should still exercise caution. For example, accessing websites with unsecured protocols (HTTP) can leave you vulnerable to man-in-the-middle attacks. Also, using Tor in combination with good security practices (like avoiding logging into accounts tied to your real identity) can ensure better protection.
Onionz is a leading brand that provides secure access to the Tor proxy network. Whether you’re looking to protect your privacy, access restricted content, or simply browse the internet with more security, Onionz offers the tools and support you need to safely navigate the web.
What is Tor Proxy?
Tor Proxy is a privacy tool that allows users to browse the internet anonymously by encrypting their traffic and routing it through a network of servers. This ensures that personal data, like IP addresses, cannot be easily tracked.
How does a Tor Proxy work?
The Tor Proxy works by routing your internet traffic through a series of multiple encrypted nodes (or “onions”). Each node only knows about the one before and after it, ensuring that your browsing remains private.
Why should I use a Tor Proxy?
You should use a Tor proxy if you value privacy and want to avoid tracking. It’s also helpful for bypassing internet censorship and accessing geo-restricted content.
Will Tor Proxy make my browsing completely anonymous?
While Tor offers strong anonymity, it’s not 100% foolproof. Users should still follow best practices (like avoiding logging into personal accounts) for enhanced security.
Where can I access the Tor Proxy?
The Tor is accessible through the Tor Browser, which is free to download and use. Websites like Onionz also help users get started with the Tor network securely.
By using a Tor , you can enjoy a safer, more private browsing experience online. Try Onionz today for top-tier anonymity and browsing security!
Onion links are part of the dark web, accessible only through the Tor network. The Tor network provides anonymity by routing traffic through multiple nodes, making it difficult to trace users' IP addresses. Accessing onion links safely is crucial as they often contain sensitive or unindexed content. Visit crown market
Accessing onion links requires careful consideration due to potential security risks. Using a secure browser like Tor ensures that your identity remains protected while navigating these sites.
Since you can't directly download the desktop version of the Tor Browser for Chrome OS from its official site, you can use alternatives:
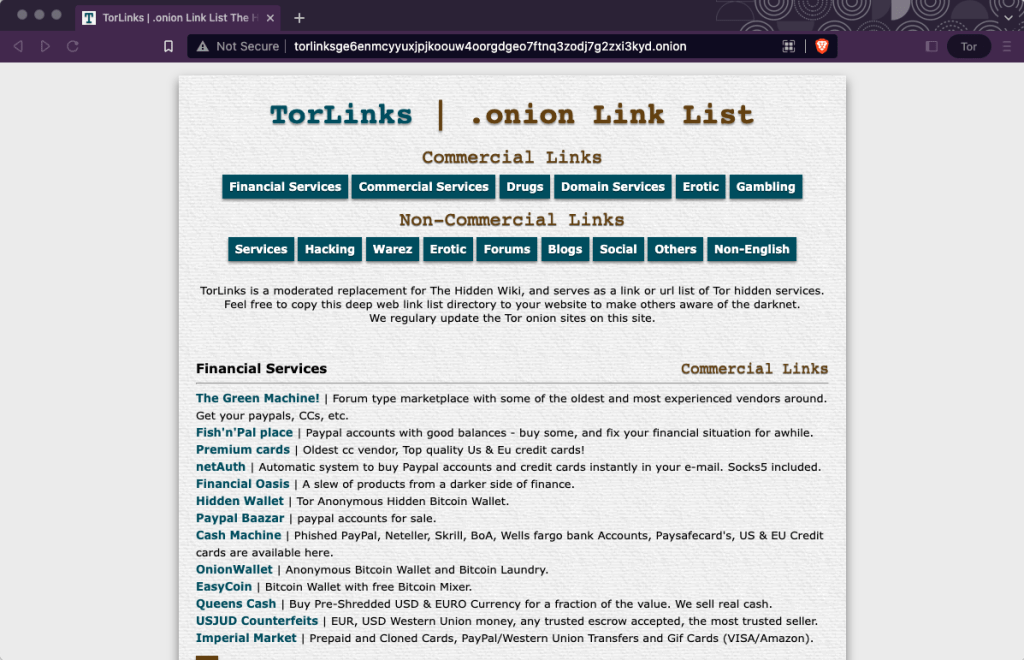
If installing a full-fledged browser isn't feasible:
However, these alternatives may not provide direct access like running a dedicated browser over the Tor network.
CROWN MARKET : gained popularity in the Dark Web due to its focus on security and privacy. It provided a secure platform for buyers and sellers, implementing features such as escrow services and encrypted communications. CrownMarket primarily dealt with drugs, Cloned cards, fake counterfeits notes offering high-quality products and reliable service to its users with super fast and discreet delivery.
crownozv6lvy373fkx44o2mxrlst4b6pu6zttcmquueomcw4onmm7oad.onion
crownipsgwzaj3eby5pienlzanam5qjreedgvvqlctlkllx7l2x4nyyd.onion
To access onion links safely on a Chromebook:
The dark web is often seen as a shadowy realm of the internet, where anonymity and secrecy rule. One of the most talked-about platforms on this hidden layer of the internet is Dread Dark Web, a forum that has become a go-to destination for many seeking privacy, freedom of speech, and access to less mainstream topics. But what exactly is Dread Dark Web, and why has it gained so much attention? Let’s explore. Visit crown market
Dread Dark Web is a decentralized, anonymous online forum located within the hidden portion of the internet known as the dark web. It is often referred to as a “dark web Reddit,” owing to its format that mimics traditional social media platforms, such as Reddit, where users can post content, comment, and interact with one another. What makes Dread Dark Web unique is that it operates on the Tor network, ensuring users’ identities and activities remain private and secure.
The forum offers a space for free speech, where individuals discuss a wide range of topics, including technology, privacy, security, and various controversial or fringe subjects. Because it exists on the dark web, access to Dread Dark Web requires specific software, such as the Tor browser, and an understanding of online privacy protocols. Visit crown market
There are several reasons why people choose to use Dread Dark Web over more mainstream online forums:
To access Dread Dark Web, you must first install the Tor browser, which is specifically designed for navigating the dark web. Once you’re connected to the Tor network, you can access Dread using its .onion address. Dread’s structure is similar to that of traditional forums, with users submitting posts, commenting, and voting on content.
However, due to the anonymous nature of the platform, users often operate under pseudonyms, adding another layer of security. This makes it difficult for law enforcement or other authorities to track users or their activities.
While Dread Dark Web shares similarities with conventional forums, there are notable differences:
While Dread Dark Web offers freedom of expression and an uncensored environment, it’s not without its risks. The dark web, in general, is known for harboring illegal activities such as hacking, trafficking, and illicit trading. As such, Dread may attract individuals involved in criminal behavior. Law enforcement agencies often monitor dark web activity, and users should be cautious about the potential consequences of engaging in illegal or harmful discussions.
CROWN MARKET : gained popularity in the Dark Web due to its focus on security and privacy. It provided a secure platform for buyers and sellers, implementing features such as escrow services and encrypted communications. CrownMarket primarily dealt with drugs, Cloned cards, fake counterfeits notes offering high-quality products and reliable service to its users with super fast and discreet delivery.
crownozv6lvy373fkx44o2mxrlst4b6pu6zttcmquueomcw4onmm7oad.onion
crownipsgwzaj3eby5pienlzanam5qjreedgvvqlctlkllx7l2x4nyyd.onion
Dread Dark Web is an anonymous online forum located on the dark web where users can discuss a variety of topics freely and securely. It operates using the Tor network to ensure privacy and anonymity for its users.
To access Dread Dark Web, you need to install the Tor browser, which allows users to access the dark web safely. Once installed, you can enter the platform’s .onion address.
People use Dread Dark Web for its privacy, freedom of speech, and the opportunity to engage in uncensored discussions. It also offers access to unique and sometimes controversial information not readily available on the surface web.
Dread is available on the dark web, and you can access it via its .onion address using the Tor browser.
Using Dread Dark Web does come with risks. While Tor ensures privacy, engaging in illegal activities or visiting malicious sites can expose you to security threats. Always practice caution and use security measures when browsing the dark web.
In conclusion, Dread Dark Web serves as a prominent platform for privacy advocates and those seeking to engage in uncensored conversations. However, with its emphasis on anonymity and open discussions, it also attracts a range of content—some legal and some not. Users must take responsibility for their activities and stay vigilant while exploring this hidden part of the internet. For those who value privacy and freedom of speech, Dread Dark Web can be an invaluable resource, but always proceed with caution. Visit crown market
Onion links are part of the dark web, accessible only through the Tor network. The Tor network provides anonymity by routing traffic through multiple nodes, making it difficult to trace users' IP addresses. Accessing onion links safely is crucial as they often contain sensitive or unindexed content.
Accessing onion links requires careful consideration due to potential security risks. Using a secure browser like Tor ensures that your identity remains protected while navigating these sites.
Since you can't directly download the desktop version of the Tor Browser for Chrome OS from its official site, you can use alternatives:

If installing a full-fledged browser isn't feasible:
However, these alternatives may not provide direct access like running a dedicated browser over the Tor network.
To access onion links safely on a Chromebook: